IT Security
- Desktop | Laptop | Server Security
- Physical Security and Audit
- Firewall and Intrusion Prevention
- Virus and Hacking Protection
GET IN TOUCH FOR IT SECURITY
Information Security Management (ISM Security)
We are in aims to gain customer satisfaction and trust by providing outstanding technology, products, and services on IT Security Services.

The aims of information security, through such efforts, are to heighten public confidence in your customer and further enhance your corporate value.
- ISM Concept
- ISM Promotion Roles
- ISM Promotion Structure
- ISM Classification
- ISM Imp. Information
- ISM Storage Format
- ISM Personal Security
- ISM Disciplinary Action
- ISM Physical Security
- ISM IT Security
- ISM Incidents / Accidents
Security safeguards the confidentiality, integrity, and availability of information from both internal and external threats. Company information includes proprietary of information, customer information, and information received from Third Parties.
Information includes that on non-electric media such as paper, or electric information stored, communicated or used, information embodied in physical property such as production facilities and prototype products.
Identify Assets
- Data Application Transaction Web Sites Directories
Evaluate Risks
- Personal Physical Operational Credential Security Excess Privilege
- Admin Accounts
- Access Rights
- Orphan Account
- Non Compliance
Manage Risk
- Personal Risk Physical Security Operation Logs E-commerce Security User Access Management
- Network Access Control
- OS Access Control
- Application Access Control
Firewall
Features
- Hybrid Firewall design for the best of all worlds.
- Application-Level Packet Filtering, both secure and efficient.
- Proxy-ARP Transparency isolates internal systems from attack.
- Policy-based routing for efficient use of dual network connections.
- Multiple redundant / balanced Internet links for fail-safe operation.
- Traffic shaping and QOS control for priority services.
- Multiple Network Boxes configured as a single fault tolerant virtual router.
- Address translation and port / address forwarding hides the internal network.

Our Firewall Solution make it easy to communicate securely with customers, partners, employees, and remote users. From advanced software solution to all-in-one integrated security appliance, Firewall family provides the flexibility to choose just the right levels of network protection.
Firewall protects servers and workstations from a host of network-level attacks, including protocol anomalies, connection flooding, denial-of-service, SYN flooding, as well as packet fragmentation evasion techniques. Black hole, fingerprint obfuscation and decoy technologies further shield protected networks from malicious probes.
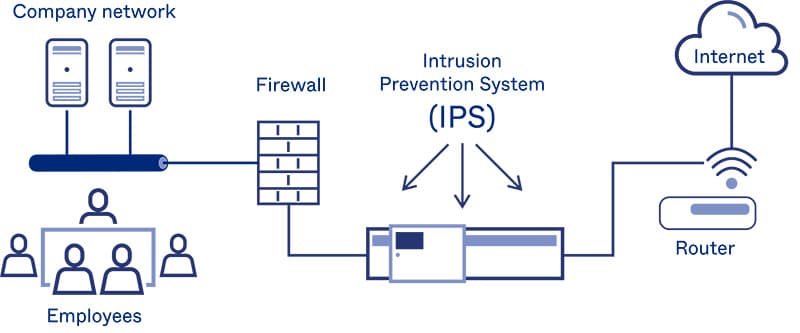
Intrusion Prevention
Features
- Intrusion Detection Engine: Zero latency, hybrid, multi-level approach that is tightly integrated with the firewall.
- Action: Active (blocks network traffic) and / or passive (logs intrusion attempts)
- Reporting: Real-time (on demand) and periodic (summary) by SMTP e-mail
- Types of Intrusion Detection: ICMP / IP, Denial of Service (DoS), portscans, protocol and application level.
- Just-In-Time and Heuristic Engines: Used to block uncharacterized attacks before they have a signature.
- Signatures: In excess of 2,500 (IDS) / 350 (IDP) – depending on configuration
Our Intrusion Protection Solutions fortify the overall security posture of today’s enterprise allowing organizations to security leverage the benefits the internet provides, Utilizing a multi-layered approach, these solutions monitor traffic, detect intrusion attempts respond to attacks in real time, and deliver flexible management capabilities to simplify administration.
Virus Protection
Virus Protection solutions safeguard the enterprise from the internet gateway to individual client PCs-and everywhere in between. Our comprehensive antivirus product family protect essential servers, desktops, remote clients, and popular messaging environments such us Microsoft Outlook/Exchange and Lotus Notes/Domino
- Home & Home Office Protect your home computers and networks, mobile devices and personal information with powerful online security solutions.
- Small Business Worry-Free™ Security Solutions automatically monitor, respond, and protect against a broad range of threats from the Internet 24/7, so you don’t have to
- Medium Business Medium-sized businesses need enterprise-strength security from the gateway to the desktop that is easy to manage and reasonably priced.
- Large Enterprise Our Enterprise Protection Strategy combines multiple layers of products and services to provide comprehensive, continuous protection at every network entry point.
- Our Solutions Antivirus Solutions for Home & Home Office, Small Business, Medium Business & Large Enterprises.
- We Support We provide consultancy services for Symantec Corporation, McAfee Inc, NOD32, Trend Micro Inc, Kaspersky Labs, CA, F-Secure Corporation, Network Associates Inc & Sophos.

Award Winning Managed Antivirus – All in One End Point Protection and Security.
